Nmap For Windows Xp Sp2
In 2014 we decided to develop the only “create your own” design portal for memorial cards & funeral programs. Funeral Prints has been printing prayer cards & funeral programs for the Metro Washington DC area for 43 years. Custom funeral program prices.
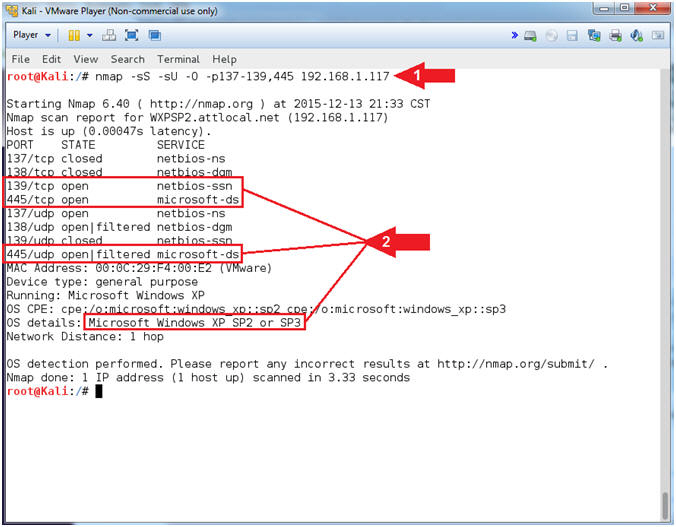
I started to read a metasploit guide book so I set up 2 Machines in VirtualBox for pen testing (host - BT 5, the second - WinXP SP2). When I m trying to scan open ports with NMAP on the Windows machine, it appears that all ports are closed, even if I turn off the Firewall. Ive tried to open SMB port through network connection center but it also didn`t help. Why all the ports are closed and how can I open some of them (at least the most common - SMB, HTTP etc)? Edit: Both of the machines working on NAT (10.0.0.x) and accept ping from each other. I tried: nmap -sS -A WinIP (also tried -sN/-sT) In each scan the result was the same - all ports are closed.
Thanks in advance! The ports you mentioned are open for specific services and servers that run on the host. If you didn't setup any servers or services on your Windows XP SP2, then there is no reason for those ports to be open on your machine, also, there is of course no reason for NMap to return a scan results claiming they are open. If you insist on using the VM you already configured I suggest you instal IIS from the 'Turn Windows features on or off' menu in the 'Add/Remove Programs' page in XPs Control Panel; or share some folder/device on the XP machine.
Hack windows xp with. Before exploiting the xp machine with metasploit it is a good idea to scan for open ports using nmap to. Windows 2003 – Service Pack 2. The latest version reported to work on Windows XP SP2/SP3 is Nmap 6.47. For older versions of Windows such as Windows 2K or XP without Service Pack 2, we recommend Nmap 5.35DC1 or older. When using Nmap on Windows 2000 (either an old version as described above, or a newer version as described later on this page), a couple dependencies from Microsoft may need to be installed first.
Another possibility instead of using a clean installation of Windows XP, is to try downloading and installing on a VM, an exploitable operating systems, preconfigured with various services and servers for practicing. Metasploitable, ICE and so on. (Check for a more comprehensive list of vulnerable applications and OS.).Disclosure, the site I'm referring to managed by me.
Nmap For Windows Xp
The NMAP scan fails because even though the firewall is disabled, when the packet gets to the OS it has nothing to do with it, so it just drops it. When you install a service on your computer it listens for certain packets on a particular port. If you were going to browse the internet on a machine, its not going to open port 80 (because web server run on port 80) but rather a port between 1023-65535. If you were to install a on your windows xp machine, it will listen for packets on port 80. NMAP should find the open port 80.